Great post. Just switched from Free LastPass to paid 1Password, happy with it so far. I know I looked at Bitwarden as well, not sure why I passed on it. But like @FestiveKnight has said, pick one and use it.
-
This site contains affiliate links. If you choose to make a purchase after clicking a link, Poker Chip Forum may receive a commission at no additional cost to you. Thank you for your support!
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
You should use a password manager (2 Viewers)
- Thread starter FestiveKnight
- Start date
Nex
Flush
You have to separate my recommendation of not using any kind of cloud services to store or transfer your confidential data from the question whether to use a password manager or not. I do recommend password managers since they make it easy to use a different random password for every site.
Syncing the password database without "cloud" by the way becomes much less of a hassle once you have keyed in all the account data you currently have. I mean, how often do you sign up for a new service... not that often. And you really can ignore recommendations to change your password for a site every X time units when you anyway use some long, completely random and individual password for each site, so there's no regular changes to existing data either. Making it a habit to only change the password database on one device (then copying and overwriting the DB on your other devices) also makes it easier.
Syncing the password database without "cloud" by the way becomes much less of a hassle once you have keyed in all the account data you currently have. I mean, how often do you sign up for a new service... not that often. And you really can ignore recommendations to change your password for a site every X time units when you anyway use some long, completely random and individual password for each site, so there's no regular changes to existing data either. Making it a habit to only change the password database on one device (then copying and overwriting the DB on your other devices) also makes it easier.
dkersey
Straight
Thanks for writing this up. This is the kick in the pants I need to do this!
Can someone comment on which is better/stronger for a master password - either a random password of letters, numbers, and symbols like this: 4Z!YFYQ4kT+ or a string of random words like this: heliport-seafarer-youthful-wrinkle-engine
buffalojim
Royal Flush
Random will always be stronger.
Pinesol13
Flush
Can someone comment on which is better/stronger for a master password - either a random password of letters, numbers, and symbols like this: 4Z!YFYQ4kT+ or a string of random words like this: heliport-seafarer-youthful-wrinkle-engine
I've read all different articles that contradict one another on this. Some say random letters, numbers and symbols are best, some some a passphrase of 3-4 random words is best. Who really knows.
Personally, I like the random combo of letters numbers and symbols. I like to use a long sentence that I can remember, and use the first letter of each word, some words can become numbers or symbols. So I end up with a 20+ character password that seems like it's random, but is still easy for me to remember.
Nex
Flush
Nex
Flush
Hypothetically, if someone knew how you generated your password (random characters or random words) then they can optimize the bruteforcing towards random words, they merely need a dictionary. So I'd mix at least one word in there that definitely does not appear in a dictionary.
My master password is a 6 word sentence (28 characters long with spaces). For those of you that have 20+ random characters, do you write them down?
I've never had a problem remembering my master password (sentence) but one thing I've done as a backup is send my wife a 3-4 sentence email and include my passphrase in there. So I have that in my sent items and she has it in her "Family" folder in her account. And no, it's not some normal email and then "Correct Horse Battery Staple!" for the last sentence!
I've never had a problem remembering my master password (sentence) but one thing I've done as a backup is send my wife a 3-4 sentence email and include my passphrase in there. So I have that in my sent items and she has it in her "Family" folder in her account. And no, it's not some normal email and then "Correct Horse Battery Staple!" for the last sentence!
As others have said, my understanding has always been that size + randomly mixing in some numbers and symbols is best and from there it doesn’t really matter if it’s only numbers and symbols or also some worlds. I default to passcode but use passphrase when I know it’s something that I may need to manually enter or read out to someone (like my fiancée). This latter is rare
Nex
Flush
What I commonly stumbled over was that many websites (particularly finance) would have a fairly low hard limit on the length of the password you could set that made it impossible to use multi-word passwords.
So my strategy ended up being generating completely random passwords with the max length allowed for those site, and a sensible number of characters for other sites. Throw all those into a password manager, encrypt the password manager database with an easy-to-remember multi-word password into which some other crap is mixed in so that a dictionary won't help much at bruteforcing it. Even one or two of the words likely aren't found in any dictionary.
So my strategy ended up being generating completely random passwords with the max length allowed for those site, and a sensible number of characters for other sites. Throw all those into a password manager, encrypt the password manager database with an easy-to-remember multi-word password into which some other crap is mixed in so that a dictionary won't help much at bruteforcing it. Even one or two of the words likely aren't found in any dictionary.
buzzmonkey
Flush
You're trying to increase your password's entropy. More characters helps, as does length. But for the master password you need to be able to remember it.
So it's completely ok to select a few random words and then strategically sprinkle in some characters.
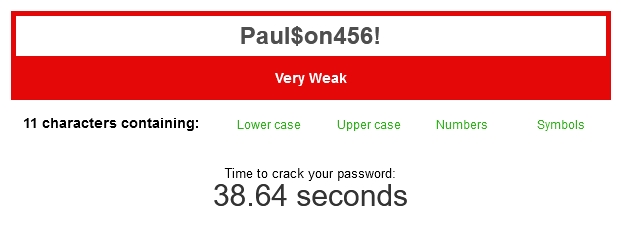
ex) pAul$0nb@nAnastUmp
That's a really strong password that you should be able to memorize in a few minutes.
So it's completely ok to select a few random words and then strategically sprinkle in some characters.
ex) pAul$0nb@nAnastUmp
That's a really strong password that you should be able to memorize in a few minutes.
Those who use LastPass should be aware of this: https://news.ycombinator.com/item?id=29705957
Seems bad!
Seems bad!
johnjohn
Full House
2fa, password mgmt. we're one more thread away from an ISO 27001 theme poker chip set.
I went to a cybersecurity seminar in my industry and one of the speakers was an ex-FBI agent that made the same point about the time that it takes to brute force a password. His point also was about the encryption on the password app.
He recommended 1Password.
When you get a password wallet, beware becoming dependent on face recognition or other crutches. I actually forgot the one password to open the password wallet...long story, but needless to say there's not a password recovery for the one password you need to open your password wallet.
He recommended 1Password.
When you get a password wallet, beware becoming dependent on face recognition or other crutches. I actually forgot the one password to open the password wallet...long story, but needless to say there's not a password recovery for the one password you need to open your password wallet.
Good write up! Worked in financial institution cybersecurity for years and free Keepass works great. After 20 years of effort we've successfully made passwords harder to remember but easy for computers to guess. (that makes me laugh from the cartoon above).  Using a long pass phrase will be better than complexity, even if relying on simpler words and no special characters, it will take longer to crack and require more computational resources than a shorter one with special characters and numbers. Even if hackers steal your encrypted password from a hacked company, they won't have the computing power and time needed to crack the password.
Using a long pass phrase will be better than complexity, even if relying on simpler words and no special characters, it will take longer to crack and require more computational resources than a shorter one with special characters and numbers. Even if hackers steal your encrypted password from a hacked company, they won't have the computing power and time needed to crack the password.
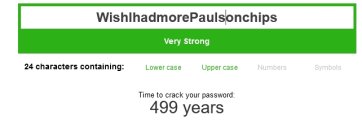
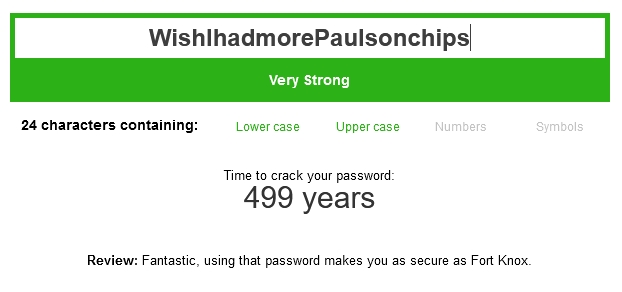
Better:
Did I just guess anyone's password?
Better:
Did I just guess anyone's password?
Attachments
Last edited:
Geremie
Full House
Is there a limit on number of characters? Could someone use a paragraph from one of their favorite books with 500+ characters?
Usually 64 or even 128 characters would take trillions of years...500+, now that's flexing it. Usually max is set in forum settings so that is a question for the admin for sure. Longer than that and there are concerns over a long password DoS, Denial of Service Attack.Is there a limit on number of characters? Could someone use a paragraph from one of their favorite books with 500+ characters?
Nex
Flush
Good write up! Worked in financial institution cybersecurity for years and free Keepass works great. After 20 years of effort we've successfully made passwords harder to remember but easy for computers to guess. (that makes me laugh from the cartoon above).Using a long pass phrase will be better than complexity, even if relying on simpler words and no special characters, it will take longer to crack and require more computational resources than a shorter one with special characters and numbers. Even if hackers steal your encrypted password from a hacked company, they won't have the computing power and time needed to crack the password.
View attachment 836432
Better:
View attachment 836435
Did I just guess anyone's password?
Pretty sure this "password strength tester" doesn't take dictionary attacks into account.
Also, while "Paulson" probably doesn't appear in a regular dictionary, if you know that the person's password is from a chip head site, you can add a custom dictionary using milieu terms.
Nex
Flush
Rate limiting can be implemented, or already is.Usually 64 or even 128 characters would take trillions of years...500+, now that's flexing it. Usually max is set in forum settings so that is a question for the admin for sure. Longer than that and there are concerns over a long password DoS, Denial of Service Attack.
Also for all hashing algorithms I know, it barely makes a difference if you hash 64 or 128 characters in terms of compute time. Hashing megabytes of data versus merely a long password, sure, that takes noticeably longer, but everything in the range of what's plausible one would manually type into a text box...
Sow, Peepel hoo spel badlee hav gud parsswerdz?Pretty sure this "password strength tester" doesn't take dictionary attacks into account.
Also, while "Paulson" probably doesn't appear in a regular dictionary, if you know that the person's password is from a chip head site, you can add a custom dictionary using milieu terms.
Last edited:
It’s better than nothing but leaves a lot to be desired. One big difference is that Google password manager doesn’t encrypt your passwords unless you change some settings but doing so breaks all the sync features. Because of this, Google could (if they wanted) go read any of your passwords right now. No one at Bitwarden could. (Somewhat a personal risk appetite question, how far do you trust Google?)
Similarly, BW is open source and Google PM is well, owned by Google, there are tons of benefits of open source software (as @Nex mentions above) but this is a big benefit to me of BW or KeePass over other options.
Lastly, BW also has a bunch of great QOL features not present in Google PM:
-customizable password generation
-notes and attachments
-storing items not tied to a website
I went back and added a few key accounts to bit warden, and added two factor authentication to these accounts as well.
Mr Winberg
Full House
My password for every site I use is "incorrect". If I ever enter the wrong password I get reminded by the error message:
"The password is incorrect"
"The password is incorrect"
Nex
Flush
buffalojim
Royal Flush
Yup, one of the reasons I stopped using LP quite a while ago. Several breaches, plus the cost.
dkersey
Straight
I downloaded bitwarden a couple of months ago but couldn't bring myself to set it all up. I finally got around to it, and now feel alot better about managing passwords.
My previous method was only working about 80% of time, which was to forward an email to myself and move it to a special folder. Some times it would be there...sometimes not.
I believe I run a relatively simple life but it turns out I put about 80 entries in it!!!
Overall I'm thinking we are better off now.
My previous method was only working about 80% of time, which was to forward an email to myself and move it to a special folder. Some times it would be there...sometimes not.
I believe I run a relatively simple life but it turns out I put about 80 entries in it!!!
Overall I'm thinking we are better off now.
buffalojim
Royal Flush
NiceI downloaded bitwarden a couple of months ago but couldn't bring myself to set it all up. I finally got around to it, and now feel alot better about managing passwords.
My previous method was only working about 80% of time, which was to forward an email to myself and move it to a special folder. Some times it would be there...sometimes not.
I believe I run a relatively simple life but it turns out I put about 80 entries in it!!!
Overall I'm thinking we are better off now.
How to use iCloud Keychain, Apple's built-in and free password manager
Also covers 2FA ability.
https://appleinsider.com/articles/2...ain-apples-built-in-and-free-password-manager
kaida
Pair
For anyone interested in trying 1Password, there's a 50% off promo for new subscribers. https://slickdeals.net/f/15437611-50-off-individuals-or-families-for-the-1st-year-at-1password
60% off for the family plan through https://1password.com/promo/wsj/
Some informational discussion in the Slickdeals thread on alternatives including open source solutions.
60% off for the family plan through https://1password.com/promo/wsj/
Some informational discussion in the Slickdeals thread on alternatives including open source solutions.
Similar threads
- Replies
- 0
- Views
- 93
- Replies
- 0
- Views
- 1K
- Replies
- 8
- Views
- 361
- Replies
- 12
- Views
- 435
- Replies
- 104
- Views
- 17K